RemoteIoT Web SSH Download: Comprehensive Guide To Secure Remote Access
RemoteIoT Web SSH Download has become an essential tool for professionals and organizations seeking secure and efficient remote access to their IoT devices. With the increasing reliance on IoT technology, managing these devices remotely is not just a convenience but a necessity. This guide will explore everything you need to know about RemoteIoT Web SSH, including its features, benefits, and how to download and use it effectively. Whether you're an IT professional, a developer, or a business owner, understanding this tool can significantly enhance your operational efficiency and security.
In today's interconnected world, the ability to access and manage IoT devices from anywhere is crucial. RemoteIoT Web SSH provides a secure and reliable solution for remote device management, allowing users to execute commands, transfer files, and monitor device performance without being physically present. This capability is particularly important for businesses that operate in multiple locations or have devices deployed in remote areas. By leveraging RemoteIoT Web SSH, organizations can reduce downtime, improve response times, and ensure their IoT infrastructure remains secure and functional.
This article will delve into the specifics of RemoteIoT Web SSH, covering its core features, security protocols, and practical applications. We'll also provide a step-by-step guide on how to download and install the software, along with tips for optimizing its use. Whether you're new to remote access tools or looking to enhance your existing setup, this comprehensive guide will equip you with the knowledge and resources you need to make informed decisions. Let's explore how RemoteIoT Web SSH can transform the way you manage your IoT devices.
Table of Contents
- Introduction to RemoteIoT Web SSH
- Key Features and Benefits
- How RemoteIoT Web SSH Works
- Step-by-Step Download Guide
- Installation and Setup Process
- Security Protocols and Best Practices
- Practical Applications and Use Cases
- Troubleshooting Common Issues
- Comparing RemoteIoT Web SSH with Alternatives
- Conclusion and Next Steps
Introduction to RemoteIoT Web SSH
RemoteIoT Web SSH is a cutting-edge tool designed to facilitate secure remote access to IoT devices through a web-based interface. This innovative solution leverages the power of SSH (Secure Shell) protocols to establish encrypted connections between users and their devices, ensuring that all data transmitted remains confidential and protected from unauthorized access. As businesses increasingly adopt IoT technology to streamline operations and enhance productivity, the need for reliable remote management tools has never been greater.
One of the primary advantages of RemoteIoT Web SSH is its user-friendly interface, which makes it accessible to both technical and non-technical users alike. Unlike traditional SSH clients that require complex configurations and command-line knowledge, RemoteIoT Web SSH provides an intuitive web-based dashboard where users can easily execute commands, transfer files, and monitor device performance. This accessibility significantly reduces the learning curve associated with remote device management and empowers organizations to maximize the potential of their IoT infrastructure.
Moreover, RemoteIoT Web SSH supports a wide range of devices and operating systems, making it a versatile solution for diverse IoT environments. Whether you're managing smart home devices, industrial sensors, or enterprise-grade servers, this tool can seamlessly integrate with your existing infrastructure. Its compatibility with various platforms ensures that businesses can maintain consistent remote access capabilities across all their devices, regardless of manufacturer or operating system. This flexibility is crucial for organizations that operate in dynamic environments where device diversity is common.
Key Features and Benefits
RemoteIoT Web SSH offers a comprehensive suite of features that address the complex needs of modern IoT management. One of its most prominent features is end-to-end encryption, which utilizes industry-standard cryptographic protocols to safeguard all communications between users and devices. This robust security framework ensures that sensitive data, including authentication credentials and operational commands, remains protected from interception and unauthorized access.
In addition to its security capabilities, RemoteIoT Web SSH provides real-time monitoring and analytics tools that enable users to track device performance and identify potential issues before they escalate. These monitoring features include customizable dashboards, alert notifications, and detailed performance metrics that help organizations maintain optimal device functionality. The platform also supports automated task scheduling, allowing users to configure routine maintenance operations and ensure consistent device health without manual intervention.
Another significant benefit of RemoteIoT Web SSH is its scalability. The platform can accommodate growing IoT networks, from small-scale deployments to enterprise-level infrastructures, without compromising performance or security. This scalability is complemented by its multi-user support system, which enables organizations to create role-based access controls and manage multiple users efficiently. Furthermore, the tool's cloud-based architecture ensures high availability and reliability, with automatic updates and backups that minimize downtime and data loss.
Advanced Security Features
Beyond basic encryption, RemoteIoT Web SSH incorporates several advanced security measures that set it apart from other remote access solutions. These include multi-factor authentication, IP whitelisting, and session recording capabilities that provide an additional layer of protection against unauthorized access. The platform also features built-in threat detection algorithms that monitor for suspicious activity and automatically trigger security protocols when potential threats are identified.
How RemoteIoT Web SSH Works
Understanding the operational mechanics of RemoteIoT Web SSH is crucial for maximizing its potential. The platform operates through a sophisticated architecture that combines web-based interfaces with secure SSH protocols. When a user initiates a connection, the system first establishes a secure tunnel using AES-256 encryption, ensuring that all subsequent communications remain protected. This initial handshake process involves multiple authentication steps, including device verification and user credential validation.
Once the secure connection is established, users can interact with their IoT devices through the web-based dashboard. The platform translates user inputs into SSH commands that are securely transmitted to the target device. This process is facilitated by a robust API infrastructure that ensures seamless communication between the web interface and device endpoints. The system also maintains persistent connections through intelligent keep-alive mechanisms, preventing unexpected disconnections during critical operations.
RemoteIoT Web SSH employs a distributed architecture that enhances performance and reliability. The platform utilizes multiple data centers strategically located across different regions, ensuring minimal latency and optimal connection speeds. This infrastructure also supports automatic failover mechanisms, where connection requests are dynamically rerouted to alternative servers in case of network disruptions or server maintenance. Additionally, the system implements advanced compression algorithms to optimize data transmission, particularly beneficial for low-bandwidth environments.
Protocol Compatibility and Integration
RemoteIoT Web SSH supports various SSH protocol versions and can seamlessly integrate with existing authentication systems, including LDAP and Active Directory. This compatibility ensures smooth implementation within enterprise environments while maintaining strict security standards. The platform also supports custom protocol extensions, allowing organizations to implement specialized security measures tailored to their specific requirements.
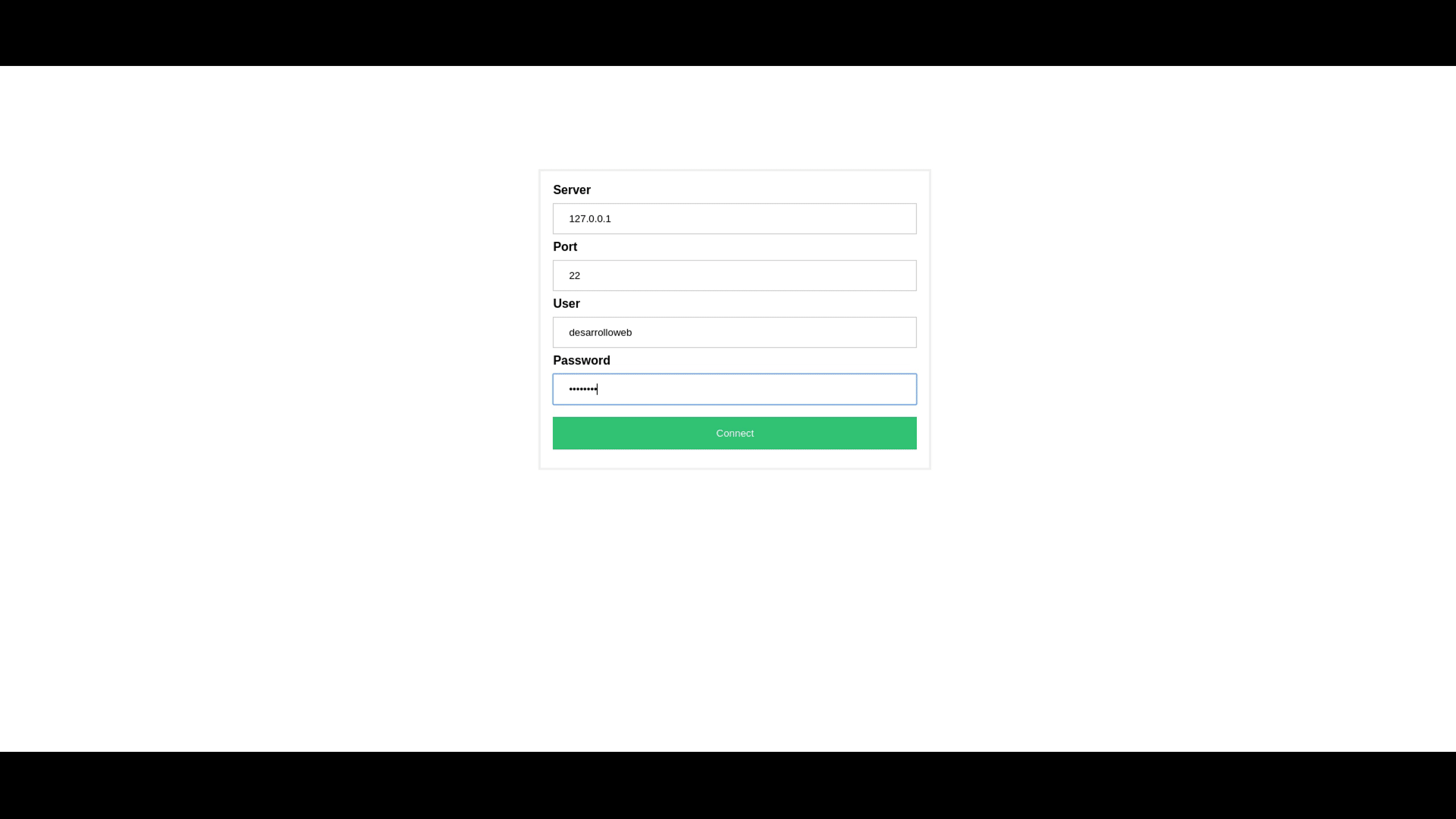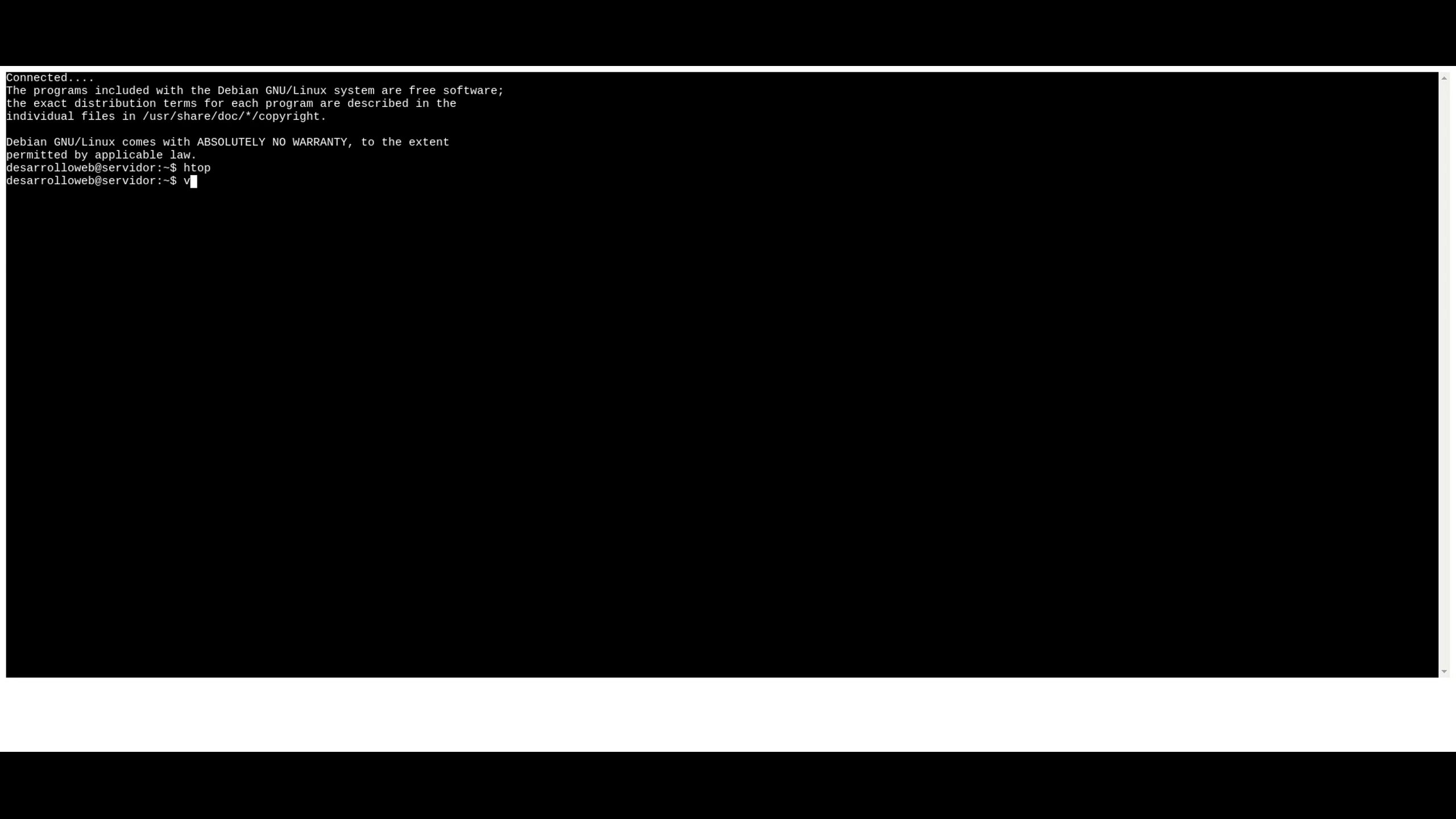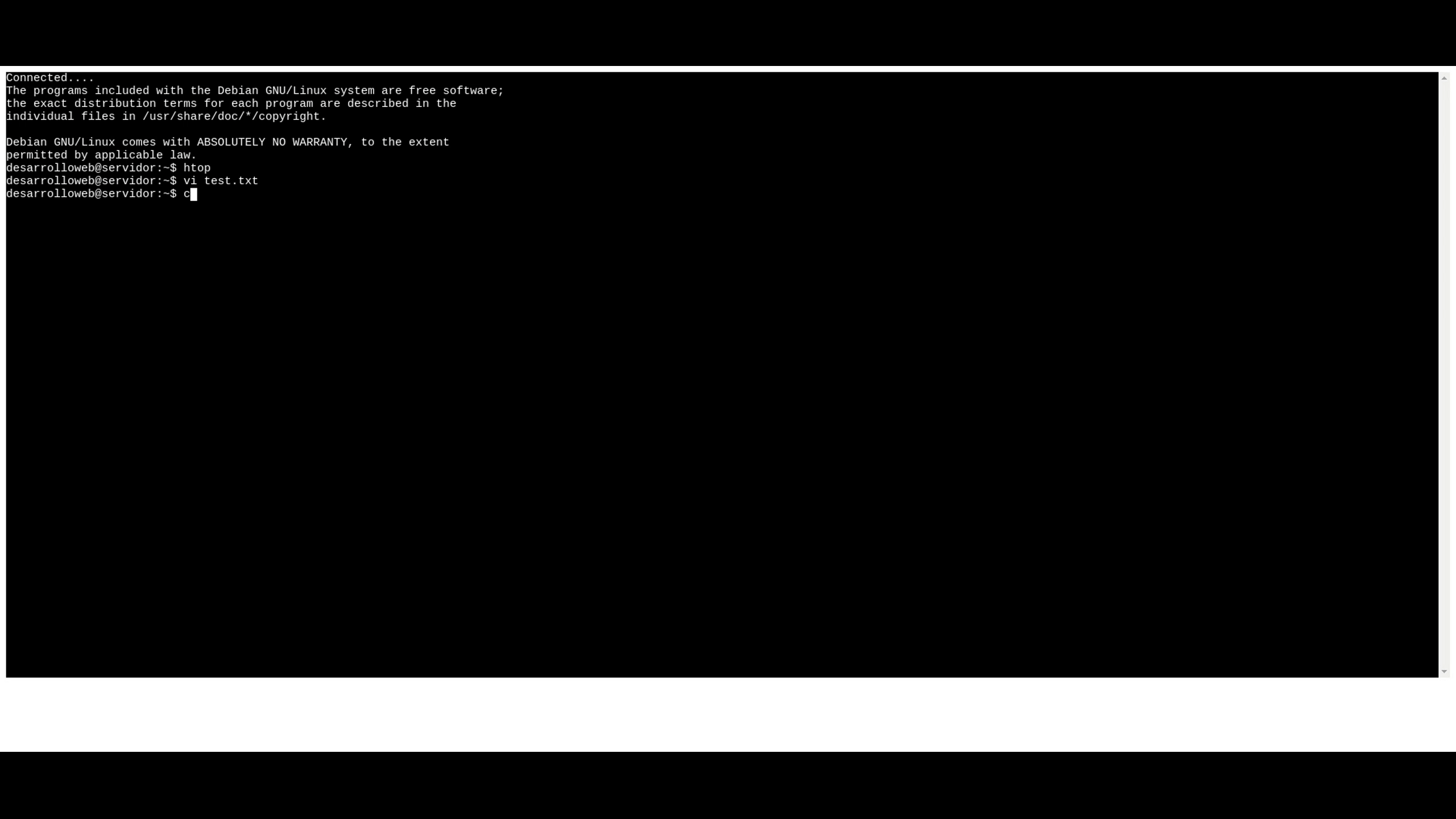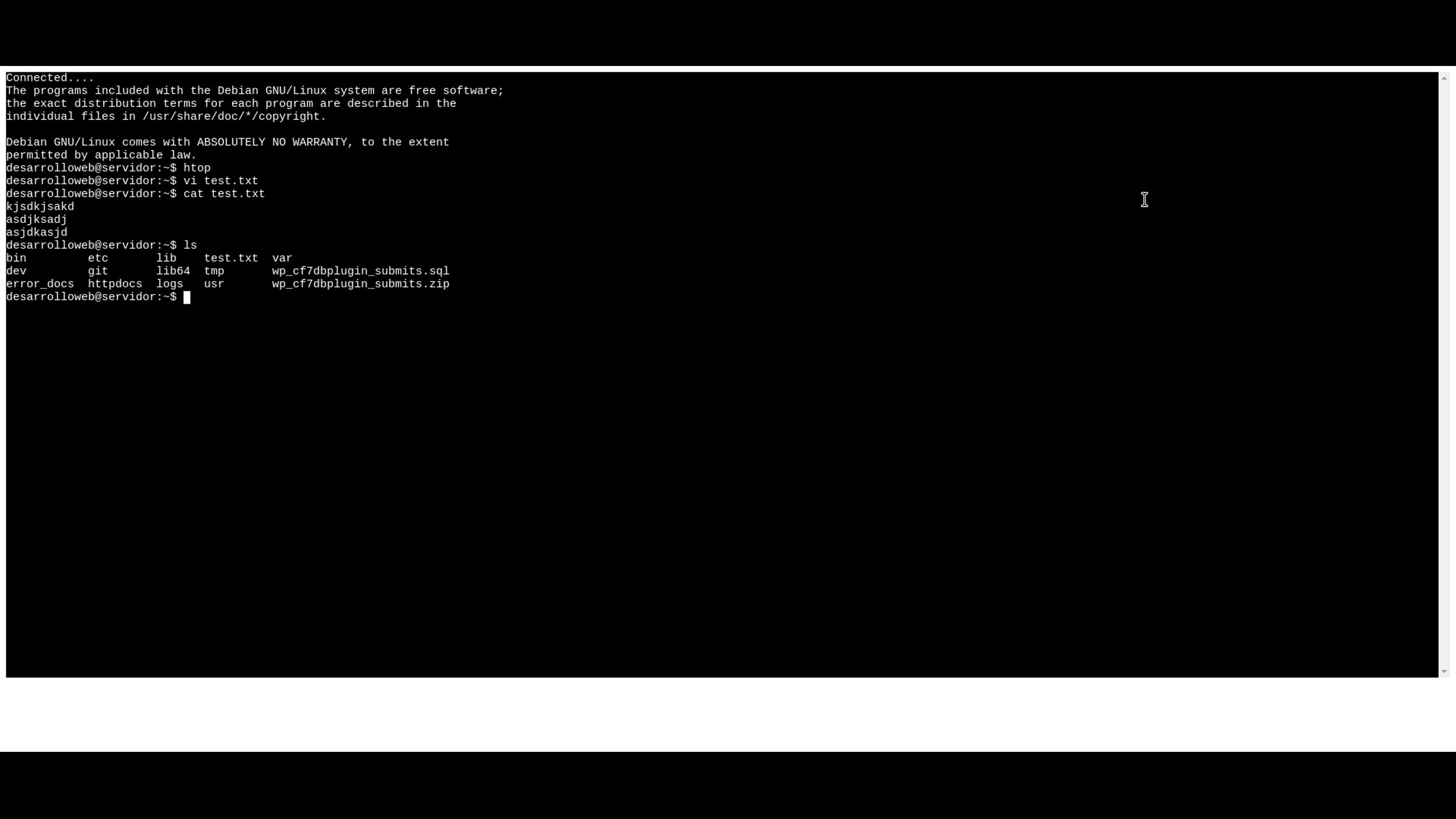
Step-by-Step Download Guide
Downloading and installing RemoteIoT Web SSH is a straightforward process designed to ensure maximum accessibility while maintaining security standards. Begin by visiting the official RemoteIoT website through a secure browser connection. Look for the dedicated download section, typically located in the main navigation menu or on the homepage. Here, you'll find multiple download options tailored to different operating systems and device types.
Before initiating the download, verify your system requirements against the platform's specifications. RemoteIoT Web SSH supports Windows, macOS, and Linux operating systems, with minimum requirements including 2GB RAM and 500MB of available storage space. For mobile users, both Android and iOS versions are available through their respective app stores. During the download process, ensure that you're connected to a secure network and that your device's antivirus software is up-to-date to prevent any potential security risks during installation.
Once the download is complete, locate the installation package in your device's download directory. For desktop installations, double-click the package file to launch the installation wizard. Follow the on-screen instructions carefully, paying particular attention to the security configuration steps. During installation, you'll be prompted to create an administrator account and configure initial security settings, including password complexity requirements and multi-factor authentication preferences. Mobile users should download the app from official stores and follow the guided setup process within the application.
Verification and Activation Process
After installation, verify the software's authenticity by checking its digital signature through your operating system's security settings. Activate your license by entering the provided key or completing the online registration process. This step is crucial for accessing premium features and receiving automatic updates. The platform will automatically check for the latest version during activation, ensuring you're running the most secure and feature-rich version available.
Installation and Setup Process
Following the initial download and installation, configuring RemoteIoT Web SSH for optimal performance requires careful attention to several critical steps. Begin by launching the application and accessing the configuration wizard, which guides users through essential setup procedures. The first step involves establishing secure connection parameters, including port configurations and encryption settings. It's recommended to use non-standard SSH ports and enable both password and key-based authentication for enhanced security.
Next, configure device discovery settings to ensure all IoT devices within your network are properly identified and registered. RemoteIoT Web SSH offers both automatic and manual device registration options. For larger deployments, utilize the automatic discovery feature while specifying network ranges and device types to streamline the process. During this phase, assign unique identifiers to each device and establish initial access permissions based on your organization's security policies.
Customize the web interface to match your operational requirements by configuring dashboard layouts, notification preferences, and monitoring parameters. The platform allows users to create custom views that display specific device metrics and performance indicators. Set up automated backup schedules and configure data retention policies to ensure compliance with organizational requirements. Additionally, establish alert thresholds and notification channels to receive real-time updates about device status and potential issues.
User Management and Role Configuration
Implement robust user management protocols by creating role-based access controls that align with your organization's hierarchy. Define specific permissions for different user groups, such as administrators, operators, and viewers. Configure multi-factor authentication requirements for each role and establish session timeout policies to enhance security. The platform supports integration with existing identity management systems, enabling seamless user provisioning and deprovisioning processes.
Security Protocols and Best Practices
Maintaining robust security is paramount when using RemoteIoT Web SSH, and implementing comprehensive security protocols is essential for protecting sensitive IoT infrastructure. The platform incorporates multiple layers of security measures, starting with its advanced encryption standards. All communications are protected using AES-256 encryption, while authentication processes utilize SHA-256 hashing algorithms to ensure data integrity. Regular security audits and penetration testing are conducted to identify and address potential vulnerabilities.
Implementing best practices begins with establishing strong password policies and enforcing multi-factor authentication across all user accounts. Utilize the platform's built-in key management system to generate and store SSH keys securely, and regularly rotate these keys according to your organization's security schedule. Configure IP whitelisting to restrict access to specific network ranges and implement session recording features to maintain comprehensive audit trails of all remote access activities.
Regular software updates are crucial for maintaining security, and RemoteIoT Web SSH provides automatic update capabilities to ensure users always run the latest version. Enable automatic backup features to protect configuration settings and historical data. Implement network segmentation strategies to isolate IoT devices from critical business systems, and configure firewall rules to control traffic flow between different network segments. Regularly review and update security policies to address emerging threats and changing operational requirements.
Compliance and Regulatory Considerations
RemoteIoT Web SSH supports compliance with various industry standards, including GDPR, HIPAA, and ISO 27001. The platform provides detailed logging and reporting features that help organizations demonstrate compliance during audits. Configure data retention policies to align with regulatory requirements, and implement role-based access controls to ensure proper handling of sensitive information. Regularly conduct security training for all users to maintain awareness of potential threats and proper security protocols.
Practical Applications and Use Cases
RemoteIoT Web SSH demonstrates its versatility through various practical applications across different industries. In manufacturing environments, the platform enables real-time monitoring and control of industrial IoT devices, allowing engineers to adjust production parameters and perform maintenance tasks remotely. This capability significantly reduces downtime and maintenance costs while improving overall equipment effectiveness. The platform's ability to handle multiple simultaneous connections makes it ideal for managing large-scale industrial deployments.
In the healthcare sector, RemoteIoT Web SSH facilitates secure remote access to medical devices and monitoring equipment. Hospitals and clinics can use the platform to maintain and troubleshoot critical medical devices without requiring physical presence, ensuring minimal disruption to patient care. The platform's robust security features meet stringent healthcare regulations, making it suitable for managing sensitive medical equipment and patient monitoring systems.
Smart city implementations benefit significantly from RemoteIoT Web SSH's capabilities. Municipal authorities can remotely manage traffic control systems, environmental sensors,

Detail Author:
- Name : Madaline Abshire
- Username : smoen
- Email : oreilly.eugenia@yahoo.com
- Birthdate : 2006-03-04
- Address : 5924 Lind Meadow Suite 176 East Mustafaburgh, MA 30466
- Phone : +1-480-760-5237
- Company : Rippin-McClure
- Job : Textile Machine Operator
- Bio : Deserunt dolorum illum voluptate aperiam non et est optio. Dicta unde mollitia est voluptas. Quidem doloremque non voluptatibus magni.
Socials
tiktok:
- url : https://tiktok.com/@leonor_official
- username : leonor_official
- bio : Ducimus praesentium et possimus. Dolore est eos perferendis.
- followers : 3373
- following : 839
linkedin:
- url : https://linkedin.com/in/leonorcremin
- username : leonorcremin
- bio : Error numquam nam vel architecto odit.
- followers : 1880
- following : 1023